1. Storage Gateway
In the simplest terms possible, Storage Gateway is a Suite of tools that give companies the ability to extend their already existent on premise databases into the cloud without a full migration.
1a. File gateway - extends your on premise file systems ( windows SMB/NFS) into amazon FSx or s3
1b. Tape Gateway - extends your backup servers (ISCSI VTL) into an s3 tape library or s3 glacier tape archive
1c. Volume Gateway - extends your block storage iscsi into aws s3, which then makes a copy via EBS

2. VPC Gateways -
VPC gateways are the main three tools that help items within your VPC connect with the outside world
2a. Internet Gateway - The internet gateway is the logical connection your VPC has to the internet. Everything connecting to the internet in your subnet is going through that gateway to get access.
2b. NAT Gateway - is a tool through which instances in a private subnet can access the internet, but external resources cannot connect with your instances
2c. Transit Gateway - A "cloud router" to connect multiple VPCs
together.
3. Endpoints:
The Endpoints are AWS services that connect your EC2 instances to AWS services through a private link
3a. VPC Interface Endpoint - A privatelink secure connection from your VPC to most AWS services (SNS, system manager, cloudtrail, cloudwatch, KMS, STS, and more)
3b. VPC Gateway Endpoint - A special privatelink secure connection from your VPC to S3 and Dynamodb
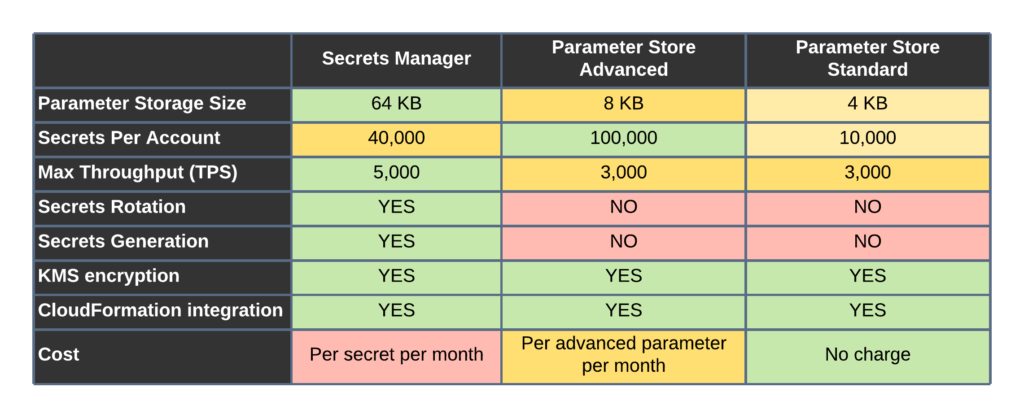
2. AWS Secrets Manager -enables you to easily rotate, manage, and retrieve database credentials, API keys, and other secrets throughout their lifecycle. Can do everything that parameter store can do, and more, including rotating keys, cross account access and generating passwords. it also costs more coming in at .40 per secret.
Secrets manager works just like parameter store in practice with more features and abilities.
Watch the videos below for cool overviews and walkthroughs of secrets manager:
- Statement is the main element of the policy, it is where it indicates the start of the actual commands of the policy
Learn More- Effect tells the policy whether you are allowing something to happen or denying it.
- It is a required element, the only values are "Allow" or "Deny"
- Action describes what specific actions you want to be denied or allowed
- - Every AWS service has its own set of spefic actions that can be placed inside this element
- Below there will be a list of the most important actions to look out for in policies
- Example: "Action": "ec2:StartInstances"
- Resource specifies the object (IAM account/service/file/other) that the statement covers
Examples:
"Resource": "arn:aws:s3:::DOC-EXAMPLE-BUCKET/*/test/*"
"Resource": "arn:aws:iam::account-ID-without-hyphens:user/Bob"
"Resource": [
"arn:aws:dynamodb:us-east-2:account-ID-without-hyphens:table/books_table", "arn:aws:dynamodb:us-east-2:account-ID-without-hyphens:table/magazines_table"
]
- The Principal elementis only used for Resource Based Policies
- Is used to specify which principals are allowed or denied access to a service.
- Principal: an AWS term for an IAM user/account/role/ AWS Service,
- Condition lets you specify conditions to when a policy is in effect.
- You can specify cool things like:
- IP address
- usernames
- MFA has to be activated and much more
created with
WYSIWYG Web Builder .